By Gideon T. Rasmussen, CISSP, CISA, CISM, CIPP
June 7, 2011
Malicious actors and the techniques they employ have continued to evolve over the past few years. The term Advanced Persistent Threat has been coined to address adversaries with the will and resources to inflict harm. Industry is preoccupied with whether or not cyber war is a credible threat. This article reflects on recent events, describes the players, inherent risk and provides practical recommendations to address threats from a business perspective.
I. Business Perspective
Business executives are concerned with the impact information security has on the bottom line. Cost is an obvious issue and productivity impact should be minimal. Executives are focused on risk management, versus security for compliance reasons. When considering a business case for a security initiative, an executive is likely to ask "What is the risk?".
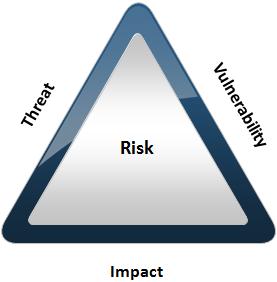 II. Business Risk
II. Business Risk
Risk comes in many forms. At a high-level, risk is the likelihood a threat will take advantage of a vulnerability, resulting in business impact. Risk mitigation consists of minimizing those essential elements through application of countermeasures or controls.
Consider business impact in the event a threat materializes and exploits a vulnerability. Within the banking industry, the Comptroller of the Currency defines risk in categories[i]:
Operational Risk: Operational risk is the risk to current or anticipated earnings or capital arising from inadequate or failed internal processes or systems, the misconduct or errors of people, and adverse external events.
Reputation Risk: Reputation risk is the risk to current or anticipated earnings, capital, or franchise/enterprise value arising from negative public opinion.
Strategic Risk: Strategic risk is the current and prospective risk to earnings or capital arising from adverse business decisions, improper implementation of decisions, or lack of responsiveness to industry changes.
Compliance Risk: Compliance risk is the risk arising from violations of, or nonconformance with, laws, rules, regulations, prescribed practices, internal policies and procedures, client agreements and other contractual arrangements, or ethical standards.
One of the basic techniques of threat management is estimating who your adversaries are. Consider their capabilities and tactics.
Hostile nation states: China is the leading country in this category. The Chinese are known for compromising intellectual property[ii] to keep their economy growing. China has been tied to Operation Aurora[iii] where dozens of organizations were targeted. Reuters recently released a report describing the threat posed by China[iv]. "Many firms whose business revolves around intellectual property -- tech firms, defense group companies, even Formula One teams -- complain that their systems are now under constant attack to extract proprietary information." China increased its international patent filings in 2010 by 56.2 percent, triple its 2006 figure[v]. Congress recently banned scientific collaboration with China, citing high espionage risks[vi].
Organized crime: Organized crime is known for compromising payment card numbers to commit fraud and generate profit. Criminal enterprises reinvest in their operations to compromise hardened targets. Card data is becoming a commodity, with a drop in street value accordingly. Theft of intellectual property is a growing trend[vii]. Competitors may use cyber mercenaries to steal trade secrets.
Insiders: Insider threat goes beyond disgruntled employees. Authorized personnel may be willing to sell company secrets for profit such as the software developer that stole proprietary code used in Goldman Sach's high-speed trading platform[viii]. Insiders can also be tricked into disclosing sensitive information through social engineering.
Whistle-Blowing Sites: WikiLeaks.org and similar websites pose a threat in the event sensitive or embarrassing data is compromised. WikiLeaks is known for publishing submissions of private, secret, and classified media from anonymous sources[ix]. They also disclose data without regard related impact such as classified U.S. government documents.
Hactivists: Hactivists are motivated by religious or political beliefs. They are unpredictable and will inflict harm without regard for profit. Anonymous is the most famous activist hactivist group. They are known for supporting WikiLeaks by launching distributed denial-of-service attacks against Amazon, PayPal, MasterCard and Visa[x]. Most recently, they attacked the U.S. Chamber of Commerce for supporting the Protect IP Act. LulzSec is an up and coming group who made headlines this year by hacking into PBS, Sony and InfraGard.
Hostile nation states and organized crime can be categorized as Advanced Persistent Threats. Hactivists and whistle-blowers can be categorized as Idealists. The combed threat of the two categories is sobering.
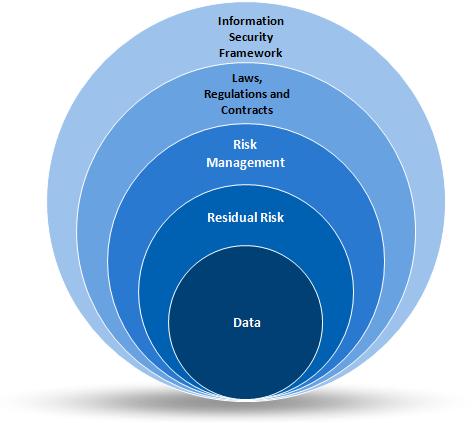 IV. Layered Program Controls
IV. Layered Program Controls
It is necessary to implement a risk-based information security program to address threats and protect the interests of the company. Start by investing in an experienced information security leader. Provide the resources necessary to protect sensitive data and ensure availability of critical business processes and services. Use layered program controls to address risk and conserve on costs.
Implement an Information Security Framework
The goals of information security are to ensure the confidentiality, integrity and availability of information. Frameworks are foundational and address controls at a mid-level. Leverage industry security standards such as ISO 27001 and COBIT. Consider this step one.
Consider Laws, Regulations and Contractual Obligations
Compliance requirements address controls at a more prescriptive level. Their deficiency lies in the bias or best interests of the governing body. For example, PCI is focused on the security of payment card data, with no regard for business continuity. SOX and HIPAA are focused on financial and health data, respectively.
Be mindful of the cost associated with compliance. Consider compliance risk when a given requirement does not make sense from an operational risk perspective. Compensating controls may be a viable alternative.
Establish a Risk Management Program
Adhering to frameworks and biased compliance requirements will not adequately protect against a determined adversary. Use risk management practices to identify, prioritize and mitigate threats that could have negative business impact.
Identify Risk Appetite
Meet with senior leaders to document the company's risk appetite. Ensure it is communicated to all personnel. NIST SP 800-60 provides a methodology to rate each type of information with impact ratings based on confidentiality, integrity and availability. Once the impact is identified, risk-based controls can be applied wherever that data is present. The ISACA Risk IT Framework provides guidance on how to establish risk appetite. Involving senior management at this early stage of the program gives them a sense of ownership and can be helpful in obtaining their active support and resources.
Identify Threats and Vulnerabilities
Compromise can occur through people, process and technology. Adversaries use technical, physical and social engineering techniques to compromise data. Subscribe to numerous security news and alert sources to identify threats and vulnerabilities. At a minimum, review US-CERT advisories, the SANS @RISK Consensus Security Alert, the DHS Daily Cyber Report and vendor security alerts. Join the U.S. Secret Service Electronic Crimes Task Force and FBI InfraGard. ECTF and InfraGard are free and provide threat and vulnerability advisories. Aggregate data into trends, such as a new hacking technique used by organized crime. Consider the impact of emerging technology such as IPv6 and quantum computing. Review lists of lists of vulnerabilities and common exploit techniques such as the SANS Top 20 and OWASP Top 10.
Risk Assessment
Conduct a risk assessment to identify which controls are needed to protect the company as a whole. Take into account known adversaries, their capabilities and compromise trends. Be mindful of the cost of each control, especially when applied throughout the enterprise. Random application of controls wastes resources and does not necessarily mitigate risk.
Have a focus on the data itself; where it is stored, processed and transmitted. Information protection controls are necessary to protect data the company depends upon for revenue. Examples include payment card numbers, customer or client information and intellectual property such as trade secrets.
Risk Assessment Methodologies
The PCI Data Security Standard[xi] describes risk assessment as "an annual process that identifies threats, and vulnerabilities, and results in a formal risk assessment. (Examples of risk assessment methodologies include but are not limited to OCTAVE, ISO 27005 and NIST SP 800-30.)".
Failure Modes and Effects Analysis (FMEA) can be used to conduct a risk assessment based upon a data flow diagram. At each system or component, consider how security controls may fail or are not present. For each failure mode, determine the severity, rate of occurrence and likelihood of detection. Those three criteria form a Risk Priority Number, which can be used to evaluate the need for control implementation. For more information on how to use FMEA to conduct a risk assessment, refer to my Payment Card Security: Risk & Control Assessments article.
Application of Controls
Significant, varied threats to business objectives require a sophisticated response. Layer preventive, corrective and detective controls as the potential for business impact increases. For example, application security techniques include secure coding practices, code reviews, automated code scans, application vulnerability scans and penetration testing. Apply all five techniques to protect high risk applications. NIST SP 800-53 provides baselines broken into high, medium and low control appendixes as an example.
Be sure to include people and process when implementing controls. Configurations must be kept current as the IT environment changes. Alerts must be monitored to be effective.
In the Gravest Extreme
When charged with protecting something extremely valuable like the secret recipe for Coke or pipeline drug formulas, conduct multiple risk assessments and implement controls as necessary. If business impact would be severe, employ extreme countermeasures such as two-person integrity or an air gap between systems and the Internet. Leave virtually no attack surface for adversaries to exploit. Defense-in-depth controls are the best way to defend against an Advanced Persistent Threat.
V. Conclusion
Now more than ever, security is a business imperative. Layered program controls are risk-based and focus expenses where the data is. That meets the needs of business leaders and security professionals. Consider the risk to your organization and take appropriate measures to mitigate it.
About the author:
Gideon T. Rasmussen is a Charlotte-based Information Security Manager with over 15 years experience in corporate and military organizations. His website is www.gideonrasmussen.com. The opinions expressed here are those of Gideon Rasmussen and do not necessarily represent those of his current or past employers.
Originally published by RiskCenter (June, 2011)